What is WordPress?
Contents
WordPress is a free and open-source content management system written in PHP and paired with a MySQL or MariaDB database. Features include a plugin architecture and a template system, referred to within WordPress as Themes.
WordPress is an application that allows you to easily build websites and publish content online.
Ways to Hack a WordPress Site And How To Prevent It
1. SQL Injections
What exactly is an SQL (Structured Query Language) injection? SQL injections are snippets of code that could be placed in an input tag within an HTML document that could affect the database associated with that document. To understand how this type of hack works, it requires some knowledge of a basic server-side scripting language like PHP and an understanding of how databases create, edit, and delete records. These details are beyond the scope of this article but here’s a good starting point for understanding SQL and PHP.
When a webpage has a user input field, the user can insert text that might resemble something like this:
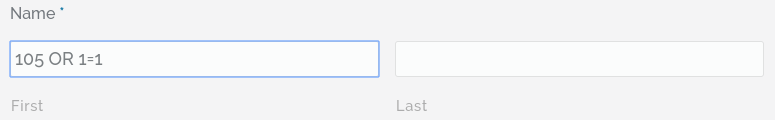
If a database is not properly protected, this simple input could wreak havoc inside the database or even reveal sensitive information to the user such as usernames and passwords.
There is a lot more one could do with SQL injections and the techniques can vary a lot based on the platform and goals of the hacker, so it’s important to protect your website or application from all possible risks.
How Does WordPress Core Defend Against SQL Injections?

Luckily for us developers, WordPress utilizes a method for sanitizing and escaping anything that is sent to the database. Using these data validation methods can help prevent most attempts of an injection by essentially filtering the input through a text parser and removing any potentially risky inputs. This is exactly what the prepare() function does! The prepare() function can even mitigate blind SQL attacks.
So if WordPress already does this, is your website at risk?
Probably not, but there is still a relatively high risk if any of these conditions apply.
- You use any plugins at all. Most high-repute plugins are generally pretty safe, but certainly not every plugin that finds its way into the repository is perfect. The more plugins you use, and the lower their quality, the higher risk your site has.
- You implement custom development, particularly anything related to forms or user input, or anything that communicates with a database.
- You do not have the latest version of WordPress, PHP, themes & plugins, or other relevant software.
How to Further Reduce Your Vulnerability to SQL Injections on Your WordPress Site
Below are a few best practices for reducing your chance of an SQL injection:
- Use a Tool to Scan for SQL Injection Vulnerabilities
- Strunk Media’s standard hosting plan utilizes a security software that automatically scans all files within a server instance that can detect SQL vulnerabilities.
- Stay Updated
- As mentioned, keeping your WP version, themes & plugins, and PHP version up-to-date is extremely important. While you can remind yourself to update these items manually, there are some available services to automate that process.
- Change Your Database Prefix
- Some injections rely on being able to guess the database prefix, which for all standard WordPress sites defaults to “wp_”. There are ways to update the prefix within your account manually, but this can be risky in itself without taking certain precautions.
- Use Trusted Themes & Plugins
- While this seems obvious, it can be difficult to decide whether or not a theme or plugin is “trusted”. An overwhelming majority of hacks come through low quality themes & plugins. Consider these factors when assessing the quality of a theme or plugin.
- Check the review average and total reviews – I generally require a 4.0 or higher and at least 10 or so reviews from different sources.
- Check the number of active installs – If your plugin only has a few dozen or even a couple hundred installs, there might be a reason it’s not so popular.
- Check the “Last updated” date – I try to avoid anything that doesn’t get updated at least every few months, or at least within the past year depending on the application.
- Check that the plugin/theme has been tested with the latest WordPress version.
- In regards to SQL Injections, form-related plugins are particularly vulnerable which is why you should be extra diligent when choosing a 3rd party plugin to provide a desired application.
- While this seems obvious, it can be difficult to decide whether or not a theme or plugin is “trusted”. An overwhelming majority of hacks come through low quality themes & plugins. Consider these factors when assessing the quality of a theme or plugin.
- Backup Your Data
- This is a suggestion for all forms of security and hardening. Having regularly saved backups won’t reduce your risk probability, but it will certainly reduce the impact of a hack by being able to restore all your data to a previously saved state.
- Further suggestions include:
- Encrypt your backups.
- Make them ‘read only’.
- Backup intervals should reflect how often your site is updated. We typically create temporary backups every week and permanent backups monthly. This varies by client and website.
- Keep an independent record of MD5 hashes.
- Keep Logs
- Logging is an important function for diagnosing bugs and other issues (such as user error) in any software environment, and hacking-related issues are no exception. There are a number of ways to enable logging and debugging in WordPress.
- Restrict Database User Privileges
- Apply the “Principle of Least Privileges” – Not every user needs the full boat of permissions!
- User prepare() for any custom development
TLDR
- Use trusted sources and stay updated
- Keep backups
- Refer to WordPress codex and security principles when making custom mods or implementing custom code


